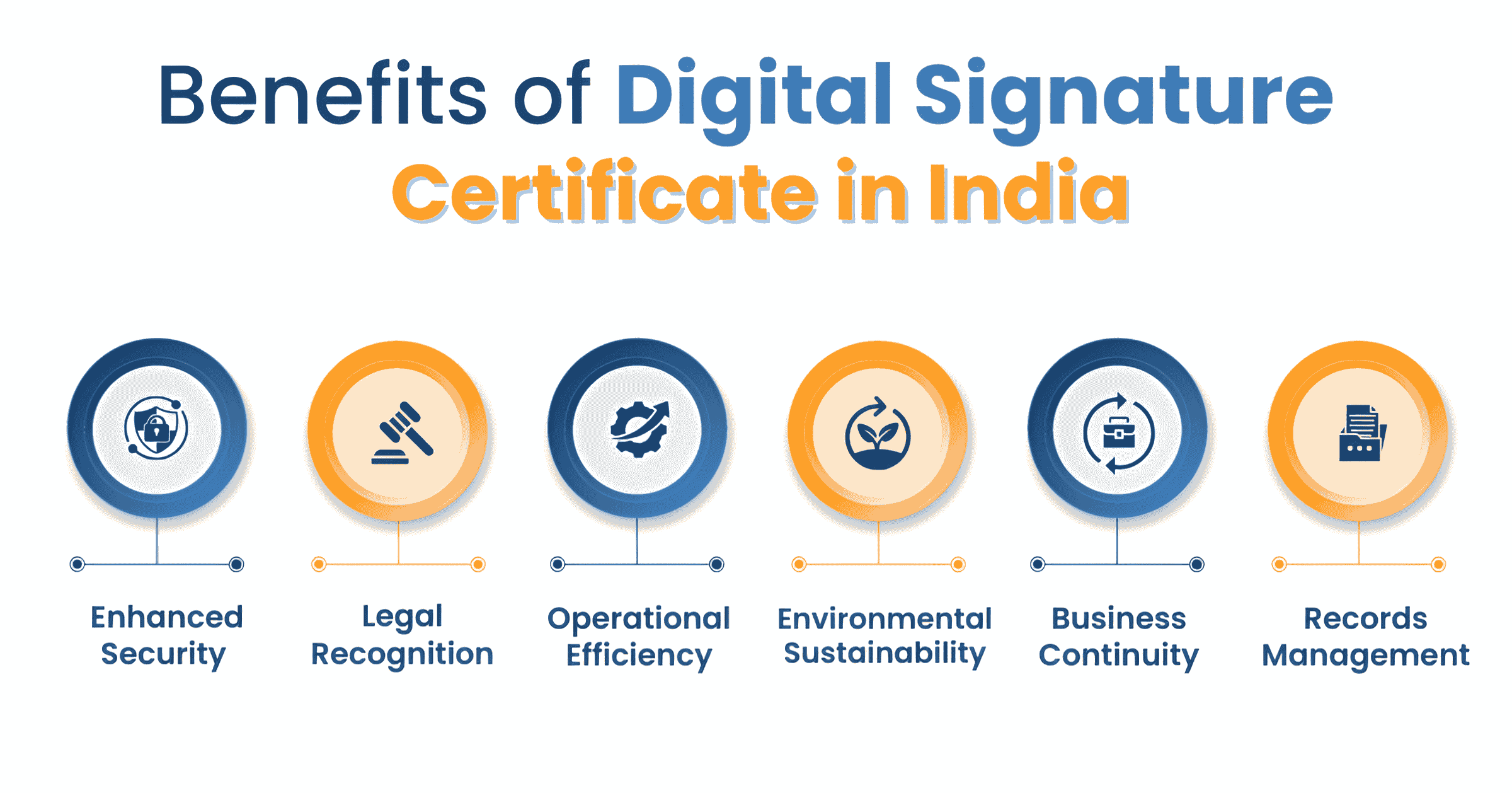
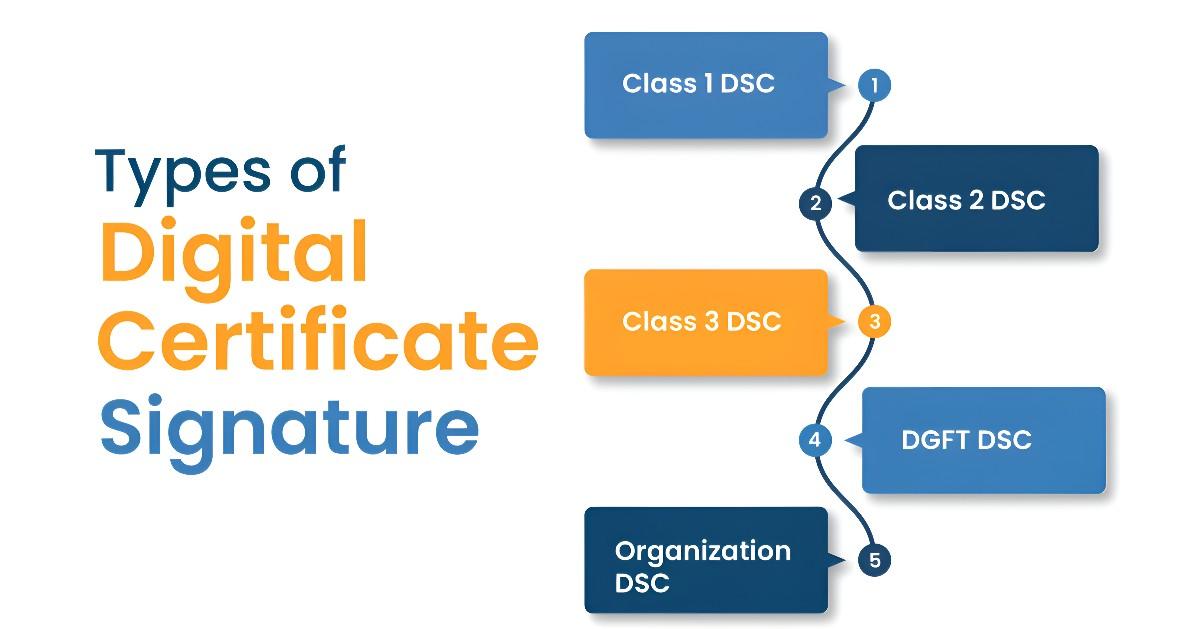
A Digital Signature Certificate (DSC) is an electronic credential that proves your identity in the digital realm. Think of it as a digital equivalent of a handwritten signature but with enhanced security and legal validity. It ensures that a digital document or transaction truly originated from you and hasn't been tampered with.
A digital signature uses cryptography to link an individual or organization to a digital document. When you "sign" a document digitally with your digital signature certificate, it creates a unique encrypted "hash" of the document. This hash is then encrypted with your private key. Anyone can verify this signature using your public key, ensuring the document's origin and that it hasn't been altered.
How a Digital Signature Certificate Secures Your Online Transactions?
A DSC secures your online transactions by leveraging Public Key Infrastructure (PKI), a framework that uses a pair of mathematically linked keys: a private key and a public key.
1. Authentication of Identity
- Verified Identity: Before issuing a DSC, a Certifying Authority (CA) rigorously verifies your identity using various methods, including Aadhaar eKYC, video verification, and document submission.
- Unique Digital Fingerprint: Your DSC contains your unique identity details. When you sign a document digitally, this signature is uniquely linked to you, acting as your verifiable digital fingerprint. This ensures that the person performing the transaction is who they claim to be, reducing the risk of impersonation and fraud.
2. Data Integrity
- Tamper-Proofing: When you digitally sign a document, the DSC creates a unique cryptographic "hash" of the document's content. This hash is then encrypted with your private key to form the digital signature.
- Detection of Alterations: If even a single character in the document is changed after it has been signed, the receiver's system will compute a different hash. When the receiver tries to verify the signature using your public key, the decrypted hash from your signature will not match the newly computed hash of the altered document. This immediately alerts the receiver to any tampering, ensuring the integrity of the data.
3. Non-Repudiation
- Undeniably Proof: Since the digital signature is uniquely created with your private key, you cannot deny having signed the document. This concept is known as non-repudiation.
- Legal Admissibility: In India, under the Information Technology Act, 2000, digital signatures are legally recognized and hold the same legal weight as a handwritten signature. This provides strong legal enforceability for online contracts, agreements, and transactions, making them admissible as evidence in a court of law.
4. Confidentiality (with Encryption DSC)
While a "Sign" DSC primarily ensures identity and integrity, an "Encrypt" DSC (or a "Sign & Encrypt" DSC) can encrypt the entire document or specific data.
This ensures that only the intended recipient, who possesses the corresponding private key, can decrypt and view the confidential information. This is particularly useful for sensitive data like financial records or personal information.
5. Timestamping
Many digital signature solutions include a secure timestamp. This verifies the exact date and time a document was signed, providing proof that the document existed in its signed state at a particular moment. This is crucial for legal and compliance purposes.
6. Audit Trails
Digital signature platforms often create audit trails that record every step of the signing process, including the signer's identity, the time of signature, and the IP address. This provides an additional layer of security and transparency, crucial for dispute resolution.
7. Reduction of Fraud and Human Error
- Automated Verification: The automated cryptographic verification process inherent in DSCs reduces the risk of forged signatures or human errors associated with manual processes.
- Efficiency: It streamlines workflows, eliminating the need for physical printing, scanning, and couriering documents, which not only saves time and cost but also minimizes opportunities for human error.
Legal Framework of Digital Signatures in India
In India, the Information Technology Act, 2000 (IT Act), serves as the cornerstone for recognizing and regulating electronic transactions, including digital signature certificates. It's important to note that while digital signature certificates have broad legal recognition, the IT Act, 2000, does specify certain exceptions where they may not be used, and a conventional wet signature is still required. These typically include:
- Contracts for the sale of immovable property.
- Power of attorney documents.
- Wills and testaments.
- Trust deeds.
- Negotiable instruments (other than cheques).
Beyond the IT Act, 2000, other critical laws that bolster the legal framework for digital signatures in India include:
- The Indian Contract Act, 1872: This Act, combined with the IT Act, allows for the formation and enforceability of contracts entered into electronically and authenticated with digital signature certificates. Section 10A specifically affirms the validity of contracts formed through electronic means, provided they satisfy all contractual conditions.
- The Indian Evidence Act, 1872: Amendments to this Act ensure that electronic records and digital signature certificates are admissible as evidence in court. Section 47A, for example, acknowledges the opinion of a Certifying Authority as a relevant fact in determining the authenticity of an electronic signature. Section 85B establishes that secure electronic records and signatures are presumed to be unaltered and authentic unless proven otherwise, reinforcing their reliability.
- Electronic Signature or Electronic Authentication Technique and Procedure Rules, 2015 (ESEATPR): These rules provide detailed procedures and criteria for electronic signatures and authentication techniques, further solidifying the framework for using a digital signature certificate online.
i) Recognized Electronic Authentication Techniques (Second Schedule):
- The Rules outline the specific techniques permitted for electronic authentication. The most prominent ones include:
- Aadhaar-based e-Sign: This popular method allows individuals to digitally sign documents remotely using their Aadhaar number, verified through OTP or biometrics. The e-Sign service facilitates the generation of the subscriber's key pair and the issuance of a short-validity DSC for one-time use.
- Digital Signatures using Asymmetric Cryptography: This refers to the traditional DSCs issued by Certifying Authorities (CAs), where a private key is stored securely on a USB token.
ii) Controller of Certifying Authorities (CCA) Role:
- The CCA is the apex regulatory body established under Section 17 of the IT Act. Its role is pivotal in the legal and technical framework for DSCs and electronic signatures in India.
- The CCA licenses and regulates the Certifying Authorities (CAs) and sets the standards for their operations, including security procedures, audit requirements, and the issuance of DSCs.
- The CCA runs the Root Certifying Authority of India (RCAI), digitally signing public keys of licensed CAs to ensure the trust and reliability of DSCs in India.
iii) Presumptions under the Indian Evidence Act, 1872 (IEA):
- The IT Act amendments integrated provisions into the IEA to bolster the legal standing of electronic records and signatures.
- Section 85A (Presumption as to electronic agreements): Creates a presumption that every electronic record purporting to be an agreement containing electronic signatures of the parties.
- Section 85B (Presumptions as to electronic records and electronic signatures):
- For "secure electronic records," the Court shall presume, unless the contrary is proved, that such a record has not been altered since the specific point of time to which its secure status relates.
- For "secure electronic signatures," the Court shall presume unless contrary is proved, that the secure electronic signature was affixed by the subscriber to sign or approve the electronic record.
- Section 85C (Presumption as to Electronic Signature Certificates): This section is highly relevant. It presumes the information in an Electronic Signature Certificate is correct unless proven otherwise and accepted by the subscriber.
This presumption significantly strengthens the legal standing and admissibility of DSCs in court.
iv) "Secure Electronic Record" and "Secure Electronic Signature":
- The IT Act and the IEA often link the presumptions of authenticity and integrity specifically to "secure electronic records" (Section 14 IT Act) and "secure electronic signatures" (Section 15 IT Act).
- These "secure" forms must meet prescribed security standards and procedures (often detailed by the CCA), ensuring a higher level of trust and legal enforceability compared to basic electronic signatures that do not adhere to such strict standards.
v) Admissibility vs. Proof:
- Though the IT Act and IEA allow electronic records and signatures as evidence, proving full authenticity may need more than this presumption.
- Section 47A of the IEA allows for expert opinion regarding the electronic signature to prove its authenticity in a dispute.
- Sections 85A, 85B, and 85C ease the proof burden for the electronic signature user, shifting it to the challenger to disprove authenticity.
vi) Context of Exceptions (Documents Excluded from Electronic Signature Use):
- Despite the legal recognition, the First Schedule of the IT Act, 2000, excludes certain types of documents and transactions from being authenticated by electronic signatures. These require traditional "wet" signatures due to their specific nature or pre-existing legal requirements:
- Negotiable Instruments (except cheques): Promissory notes, bills of exchange.
- Power of Attorney.
- Trust Deeds.
- Wills and other Testamentary Dispositions.
- Any contract for the sale or conveyance of immovable property or any interest in such property.
- These exceptions exist because some documents require registration under other laws, like the Registration Act, 1908, which requires physical presence and wet signatures. Additionally, highly personal or testamentary documents demand a very high standard of proof of intent.